OpenSSL命令学习
一、 基础概念
一个X.509中的证书所有者和发行者信息如下图,请指出下列字段的含义
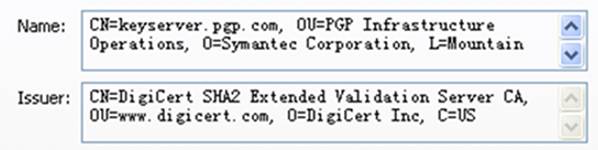
| CN:通用名称 | O:机构名 | C:国名 |
|---|---|---|
| OU:机构单元名称 | L:地理位置 |
二、 加解密
1. 创建新文件test,对其进行对称加解密
echo hello,openssl > test
openssl enc -des3 -e -a -in ./test -out test.enc #加密
openssl enc -d -des3 -a -in ./test.enc #解密
利用OpenSSL作对称加密需要使用其子命令enc,其用法为:
openssl enc -ciphername [-in filename] [-out filename] [-pass arg] [-e] [-d] [-a/-base64] [-A] [-k password] [-kfile filename] [-K key] [-iv IV] [-S salt] [-salt] [-nosalt] [-z] [-md] [-p] [-P] [-bufsize number] [-nopad] [-debug] [-none] [-engine id]
其中常用选项有
-e:加密; -d:解密; -ciphername:ciphername为相应的对称加密算命名字,如-des3、-ase128、-cast、-blowfish等等。 -a/-base64:使用base-64位编码格式; -salt:自动插入一个随机数作为文件内容加密,默认选项; -in FILENAME:指定要加密的文件的存放路径; -out FILENAME:指定加密后的文件的存放路径;
2. 计算文件test的摘要
openssl dgst test
dgst是openssl单向加密的命令,其用法为:
openssl dgst [-md5 -md4 -md2 -sha1 -sha -mdc2 -ripemd160 -dss1] [-c] [-d] [-hex] [-binary] [-out filename] [-sign filename] [-keyform arg] [-passin arg] [-verify filename] [-prverify filename] [-signature filename] [-hmac key] [file…]
其中常用选项有
[-md5|-md4|-md2|-sha1|-sha|-mdc2|-ripemd160|-dss1]:指定一种单向加密算法; -out FILENAME:将加密的内容保存到指定的文件中;
OpenSSL还支持生成密码的hash离散值,其子命令为passwd,语法如下:
openssl passwd [-crypt] [-1] [-apr1] [-salt string] [-in file] [-stdin] [-noverify] [-quiet] [-table] {password}
常用选项为:
-salt STRING:添加随机数; -in FILE:对输入的文件内容进行加密; -stdin:对标准输入的内容进行加密;
三、证书
1. 签发CA自签名证书
openssl version -a #查看openssl的基本信息
#可找到openssl.cnf配置文件位于目录/usr/lib/ssl
cd /usr/lib/ssl
mkdir certs crl newcerts private
touch index.txt serial
ls -l #查看其中的内容
openssl genrsa -des3 -out private/cakey.pem 512 #生成CA证书的私钥
openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 730 #生成CA自签名证书
上面openssl命令的子命令genrsa生成私钥,然后再使用子命令rsa私钥中提取公钥。 genrsa的语法如下:
openssl genrsa [-out filename] [-passout arg] [-des] [-des3] [-idea] [-f4] [-3] [-rand file(s)] [-engine id] [numbits]
常用选项:
-out FILENAME:将生成的私钥保存至指定的文件中; [-des] [-des3] [-idea]:指定加密算法; numbits:指明生成的私钥大小,默认是512;
另外,还可以用rsa子命令提取公钥,rsa的语法如下:
openssl rsa [-inform PEM NET DER] [-outform PEM NET DER] [-in filename] [-passin arg] [-out filename] [-passout arg] [-sgckey] [-des] [-des3] [-idea] [-text] [-noout] [-modulus] [-check] [-pubin] [-pubout] [-engine id]
常用选项为:
-in FILENAME:指明私钥文件的存放路径; -out FILENAME:指明将公钥的保存路径; -pubout:根据提供的私钥,从中提取出公钥;
上面还利用了req命令生成证书,req主要用于创建和处理证书请求,语法如下:
openssl req [-help] [-inform PEM DER] [-outform PEM DER] [-in filename] [-passin arg] [-out filename] [-passout arg] [-text] [-pubkey] [-noout] [-verify] [-modulus] [-new] [-rand file…] [-writerand file] [-newkey rsa:bits] [-newkey alg:file] [-nodes] [-key filename] [-keyform PEM DER] [-keyout filename] [-keygen_engine id] [-digest] [-config filename] [-multivalue-rdn] [-x509] [-days n] [-set_serial n] [-newhdr] [-addext ext] [-extensions section] [-reqexts section] [-precert] [-utf8] [-nameopt] [-reqopt] [-subject] [-subj arg] [-sigopt nm:v] [-batch] [-verbose] [-engine id]
我们用到的选项有:
-new:表示生成一个新的证书签署请求; -x509:专用于生成CA自签证书; -key:指定生成证书用到的私钥文件; -out FILNAME:指定生成的证书的保存路径; -days:指定证书的有效期限,单位为day,默认是365天;
2. 生成私钥长度为512,有效期为2年的客户证书。(包括生成私钥、生成证书申请、签发证书命令)
openssl genrsa -des3 -out app.key 512 #生成应用证书私钥
openssl req -new -key app.key -out app.csr #生成证书签名请求
echo 00 > serial
openssl ca -cert cacert.pem -keyfile private/cakey.pem -config ../openssl.cnf -in app.csr -out app.crt -days 730
上面用到了子命令ca,用于在ca服务器上签署和吊销证书,并生成crl,还维护已颁发证书的文本数据库及状态,语法如下:
openssl ca [-help] [-verbose] [-config filename] [-name section] [-gencrl] [-revoke file] [-valid file] [-status serial] [-updatedb] [-crl_reason reason] [-crl_hold instruction] [-crl_compromise time] [-crl_CA_compromise time] [-crldays days] [-crlhours hours] [-crlexts section] [-startdate date] [-enddate date] [-days arg] [-md arg] [-policy arg] [-keyfile arg] [-keyform PEM DER] [-key arg] [-passin arg] [-cert file] [-selfsign] [-in file] [-out file] [-notext] [-outdir dir] [-infiles] [-spkac file] [-ss_cert file] [-preserveDN] [-noemailDN] [-batch] [-msie_hack] [-extensions section] [-extfile section] [-engine id] [-subj arg] [-utf8] [-sigopt nm:v] [-create_serial] [-rand_serial] [-multivalue-rdn] [-rand file…] [-writerand file]
用到的选项有
-cert :ca证书文件 -keyfile :用来签名请求的私钥 -config :配置文件 -revoke :要撤销证书的文件名 -gencrl:生成crl文件
另外,可以用x509查看证书
openssl x509 -in app.crt -noout =serial -dates -subject
-noout:不输出加密的证书内容; -serial:输出证书序列号; -dates:显示证书有效期的开始和终止时间; -subject:输出证书的subject;
3. 撤销客户证书
openssl ca -revoke cacert.pem
echo 00 > crlnumber
4. 发布CRL
openssl ca -gencrl -out ca.crl #发布crl
openssl crl -in ca.crl -noout -text #查看crl
参考:
官方文档: https://www.openssl.org/docs/man1.1.1/man1/ 小尛酒窝的简书: https://www.jianshu.com/p/e311a6537467